- Details
- Hits: 526946

By Rob Mitchell
A case study of a successful phishing (possibly spearphishing) expedition
Background:
Phishing is a social engineering attack involving the presentation of a fake web page to the victim (the Mark) that convinces him or her to enter personal information that may include website logon credentials, security questions and answers, Social Security number, Credit Card numbers, Financial information or other sensitive information the attacker can use to access the Mark's online account, use the Mark's money to make purchases or engage in other illicit activities. The bait can be delivered through various means, but the most common methods are email messages or web page pop-ups.
Spearphishing is phishing that is targeted toward a specific individual, group, or other identifiable entity. A phishing message will have content that is generalized, whereas a spearphishing message is personalized toward the Mark and may contain specific information intended to make the Mark think that the message came from a source that has bonafide contact with the Mark.
The attack which resulted in compromise of John Podesta's Gmail account was definitely a phishing attack and was probably part of a spearphishing campaign. This article will attempt to create a timeline of events of exactly what happened.
People and organizations involved
Hillary For America (HFA) is the legal entity name for Hillary Clinton's Presidential Campaign.
John Podesta: Chairman of HFA
Sara Latham: Chief of Staff to John Podesta at HFA
Shane Hable: CIO at HFA
Milia Fisher: Special Assistant at HFA
Charles Delavan: IT Helpdesk Manager at HFA
Events in the order they occurred
Saturday, March 19, 2016
04:34:30 AM EDT
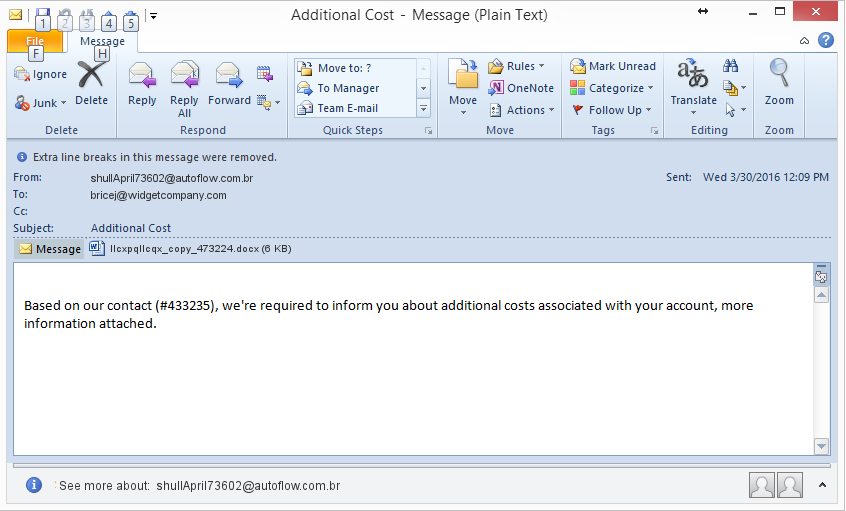
An email message arrived in John Podesta's Gmail account (This email address is being protected from spambots. You need JavaScript enabled to view it.)
*** quoted message begins ***
Saturday, March 19, 2016 at 4:34:30 AM EDT
Podesta's Gmail box received the following message ostensibly from Google:
> *From:* Google <This email address is being protected from spambots. You need JavaScript enabled to view it.;
> *Date:* March 19, 2016 at 4:34:30 AM EDT
> *To:* This email address is being protected from spambots. You need JavaScript enabled to view it.
> *Subject:* *Sоmeоne has your passwоrd*
> Sоmeоne has your passwоrd
> Hi John
> Someone just used your password to try to sign in to your Google Account
> This email address is being protected from spambots. You need JavaScript enabled to view it..
> Details:
> Saturday, 19 March, 8:34:30 UTC
> IP Address: 134.249.139.239
> Location: Ukraine
> Google stopped this sign-in attempt. You should change your password
> immediately.
> CHANGE PASSWORD <https://bit.ly/1PibSU0>
> Best,
> The Gmail Team
*** quoted message ends ***
Discussion/Analysis:
The original message is not contained in the published Wikileaks archive. It is quoted in an email discussion between HFA staff members. The original message headers would have contained additional information about the originating IP address of the message, but since the only copy of the original message published is inside a forwarded message it is not possible to do analysis on the original headers. Even if the original headers were available, it is likely the sender used either TOR (The Onion Router) or a VPN (Virtual Private Network) to conceal his IP address and therefore his location.
However the Change Password link shows the message to be a fake.
The link goes to the URL (Web address) https://bit.ly/1PibSU0 which has been shortened using the bit.ly URL shortener.
Although Google often shortens URLs in its system messages, it has its own URL shortener with links that begin with goo.gl, not bit.ly.
Expanded, the bit.ly/1PibSU0 link expands to the following URL:
https://bitly.com/a/warning?hash=1PibSU0&url=http%3A%2F%2Fmyaccount.google.com-securitysettingpage.tk%2Fsecurity%2Fsigninoptions%2Fpassword%3Fe%3Dam9obi5wb2Rlc3RhQGdtYWlsLmNvbQ%253D%253D%26fn%3DSm9obiBQb2Rlc3Rh%26n%3DSm9obg%253D%253D%26img%3DLy9saDQuZ29vZ2xldXNlcmNvbnRlbnQuY29tLy1RZVlPbHJkVGp2WS9BQUFBQUFBQUFBSS9BQUFBQUFBQUFCTS9CQldVOVQ0bUZUWS9waG90by5qcGc%253D%26id%3D1sutlodlwe
When control code is eliminated, the URL goes to an address in the domain
myaccount.google.com-securitysettingpage.tk
This is not an address at Google, but a fake web server. The last part of the URL, .tk is a top level domain (TLD) for the Tokelau territory of New Zealand. A fake web server can be set up in any TLD, but the .tk TLD has one feature of interest to hackers: It offers free domain registration with minimal information disclosure.
A web registration page for the free .TK Domain at http://www.dot.tk/en/index.html?lang=en has ad text which reads:
"Dot TK is a FREE domain registry for all websites on the Internet. It has exactly the same power as other domain extensions, but it's free! Because it's free, millions of others have been using .TK domains since 2001 - which makes .TK powerful and very recognizable."
The availability of free Internet domain registration makes the .tk TLD very attractive to hackers and cybercriminals.
The message claims that someone unknown accessed Podesta's Gmail account from an IP address in Ukraine:
134.249.139.239
This address resolves to a Ukrainian Mobile Phone operator Kvivstar GSM in Kyiv. Further analysis shows that the address resolves to an account in Dnepropetrovsk, on the Dniepr River a hundred miles north of the Sea of Azov in Southeastern Ukraine.
But this information is useless because it's a fake address in a fake email message. It's just there to throw off the ignorant. If it was the Russians, using a Ukraine address as a red herring is a nice touch.
Saturday Morning, March 19, 2016 - Sara Latham forwards the message (1st forward)
Sara Latham accesses Podesta's Gmail account and sees the fake message. She forwarded the message or at least the body content of the message to Charles Delavan, the HFA Help Desk Manager. The message sent from Latham to Delavan is not in the Wikileaks archive, from which we can infer that Latham forwarded the message text from her own HFA email account.
Saturday Morning 09:54 AM - Charles Delavan replies to Latham (2nd forward)
Charles Delavan responds to Sara Latham
*** quoted message begins ***
*From:* Charles Delavan <This email address is being protected from spambots. You need JavaScript enabled to view it.;
*Date:* March 19, 2016 at 9:54:05 AM EDT
*To:* Sara Latham <This email address is being protected from spambots. You need JavaScript enabled to view it.;, Shane Hable <
This email address is being protected from spambots. You need JavaScript enabled to view it.>
*Subject:* *Re: Sоmeоne has your passwоrd*
Sara,
This is a legitimate email. John needs to change his password immediately,
and ensure that two-factor authentication is turned on his account.
He can go to this link: https://myaccount.google.com/security to do both.
It is absolutely imperative that this is done ASAP.
If you or he has any questions, please reach out to me at 410.562.9762
*** copied message thread redacted to avoid confusion ***
-Charles Delavan
HFA Help Desk
The HFA Operations Team is here to support you. Let us know how we’re doing
by filling out a brief survey <http://bit.ly/1gL3oMk>.
*** quoted message ends ***
Discussion/Analysis
Delavan sent Latham a link to Google's actual security page, where Podesta or one of his staff could have changed his password. He also sent a copy of his message with the proper response to Shane Hable, his boss.
Saturday afternoon, 12:07 - Latham forwards Delavan's message to Milia Fisher (3rd forward)
Sara Latham forwarded Delavan's message to Milia Fisher
*** quoted message begins - Here I include the entire message thread sent from Sara Latham to Milia Fisher to show how the mistake was made which gave the attacker access to Podesta's email***
From:This email address is being protected from spambots. You need JavaScript enabled to view it.
To: This email address is being protected from spambots. You need JavaScript enabled to view it., This email address is being protected from spambots. You need JavaScript enabled to view it.
Date: 2016-03-19 12:07
Subject: Fwd: Sоmeоne has your passwоrd
The gmail one is REAL
Milia, can you change - does JDP have the 2 step verification or do we need
to do with him on the phone? Don't want to lock him out of his in box!
Sent from my iPhone
*** Delavan's message with the real Google Password reset link begins ***
Begin forwarded message:
*From:* Charles Delavan <This email address is being protected from spambots. You need JavaScript enabled to view it.;
*Date:* March 19, 2016 at 9:54:05 AM EDT
*To:* Sara Latham <This email address is being protected from spambots. You need JavaScript enabled to view it.;, Shane Hable <
This email address is being protected from spambots. You need JavaScript enabled to view it.>
*Subject:* *Re: Sоmeоne has your passwоrd*
Sara,
This is a legitimate email. John needs to change his password immediately,
and ensure that two-factor authentication is turned on his account.
He can go to this link: https://myaccount.google.com/security to do both.
It is absolutely imperative that this is done ASAP.
If you or he has any questions, please reach out to me at 410.562.9762
*** Delavan's forwarded message ends. The copy of the original phishing message that got forwarded to Delavan begins here, copied inside Latham's earlier forwarded message ***
On Sat, Mar 19, 2016 at 9:29 AM, Sara Latham <This email address is being protected from spambots. You need JavaScript enabled to view it.;
wrote:
>
>
> Sent from my iPhone
>
> Begin forwarded message:
>
> *From:* Google <This email address is being protected from spambots. You need JavaScript enabled to view it.;
> *Date:* March 19, 2016 at 4:34:30 AM EDT
> *To:* This email address is being protected from spambots. You need JavaScript enabled to view it.
> *Subject:* *Sоmeоne has your passwоrd*
>
> Sоmeоne has your passwоrd
> Hi John
>
> Someone just used your password to try to sign in to your Google Account
> This email address is being protected from spambots. You need JavaScript enabled to view it..
>
> Details:
> Saturday, 19 March, 8:34:30 UTC
> IP Address: 134.249.139.239
> Location: Ukraine
>
> Google stopped this sign-in attempt. You should change your password
> immediately.
>
> CHANGE PASSWORD <https://bit.ly/1PibSU0>
>
> Best,
> The Gmail Team
> You received this mandatory email service announcement to update you about
> important changes to your Google product or account.
>
*** Forwarded message ends, Delavan's signature block begins ***
--
-Charles Delavan
HFA Help Desk
The HFA Operations Team is here to support you. Let us know how we’re doing
by filling out a brief survey <http://bit.ly/1gL3oMk>.
*** quoted message ends ***
Saturday afternoon, 12:14pm - Fisher replies with full thread (4th forward)
Milia Fisher replied back seven minutes later:
*** quoted message begins ***
From:This email address is being protected from spambots. You need JavaScript enabled to view it.
To: This email address is being protected from spambots. You need JavaScript enabled to view it.
CC: This email address is being protected from spambots. You need JavaScript enabled to view it.
Date: 2016-03-19 12:14
Subject: Re: Sоmeоne has your passwоrd
Hi- yes I will call John right away and work on new passwords. He will need
to use my two step verification codes to sign in.
Milia Fisher
(858) 395-1741
On Mar 19, 2016, at 10:07 AM, Sara Latham <This email address is being protected from spambots. You need JavaScript enabled to view it.;
wrote:
*** The entire message thread including the original phishing message with the fake password reset link and Delavan's message with the actual Google password reset link was sent to Milia Fisher. They are deleted here for brevity but can be seen above ***
*** quoted message ends ***
Discussion/Analysis
Milia Fisher evidently made good on her promise to contact Podesta, but it looks like Podesta clicked on the FAKE link in the original phishing message to reset his password instead of the GOOD link sent by Delavan. When Podesta clicked on the phishing link instead of following the instructions of Delavan he handed his email to the attacker.
What follows is conjecture, but it is based on of what the attacker could have done with Podesta's Gmail in order to obtain the email archive that ended up being published by Wikileaks.
As soon as Podesta input his new password in the fake web page in the .tk domain, the fake website would have used a scripted process to change Podesta's real Gmail account password immediately. This would ensure Podesta could continue to use the account normally.
Although Milia Fisher's message mentions two step verification codes, it doesn't look like Podesta's personal Gmail account used them. Email for the hillaryclinton.com domain used by HFA is set up using Google's Gsuite for non-profits and would probably use two-step verification for additional security. Fisher's remarks and the end result of Podesta's compromised personal Gmail (not HFA) email account being breached by the attacker are consistent with Podesta having an official HFA account that used two-step verification, while his personal free Gmail account did not.
This is another illustration about why it is not a good idea to use personal accounts for business purposes, especially for someone who is a technological neophyte, as Podesta appears to have been.
What did the attacker do?
What follows is conjecture, but given the technology available, it is one way the attacker could have obtained a full archive of Podesta's email.
First, the attacker could use an Internet connection routed through TOR or a VPN connection. An VPN server or TOR exit node in Amazon's Cloud in Ashburn, Virginia near Washington DC would not alert security protocols the way an overseas connection would. The attacker could have immediately logged onto Podesta's email account and could have used a service called Google Takeout to download a complete archive of Podesta's email.
Google Takeout downloads email as a Zip file archive which contains a set of files in the MBOX format, one MBOX for each email Label or Folder. The MBOX container files contain individual emails in the .eml file format, which include the entire raw message including the technical headers that are used to route email from sender to recipient. Google Takeout would be my choice at any rate, since it downloads the archive to the web browser session which originated the Takeout session and download request.
And that's it. Every few days the attacker could log on again taking the same security measures but repeat the archive download, limiting the archive to new messages since the last download. The attacker could also use Google Takeout to access any other Google data stored on the account, for instance Google Drive docs. It seems fairly unlikely he did this becaue Podesta sounds like a low-end Gmail user who is probably unaware of the vast capabilities of a free Gmail account. It is also unlikely since the Wikileaks Podesta archive contained only emails, unless there actually was data from other sources there that lacked any newsworthy information.
The attacker could have made an IMAP connection to the account using an email client like Outlook or Thunderbird, but Google Takeout would have been much more efficient and discrete, so I think it's safe to say this is the most likely method used to download Podesta's email.
The attacker could repeat the process every few days. When someone finally got around to checking they could look at the Google Takeout archive history and see what was downloaded, but by then it would be too late.
Is there any evidence of who sent the attack email?
This was a fairly low-tech attack. Many high schoolers could have pulled it off. The attacker didn't have to spend much money. The comsecuritysettingpage.tk domain used for the fake website was registered for free. I can't find out anything about where the fake website was hosted, all I can tell is that it is no longer hosted anywhere. The registry information from the RIPE.NET NCC simply tells us the domain registry has reverted to the .TK registry
The attacker showed some sophistication. The domain name is a good one to spoof neophytes, but it was not hard to register. Nor would the fake website have been difficult to set up. Most of the fake site could be copied directly from Google, even using Google's own graphics on their own servers. The only thing changed on the fake site is the bit.ly link from a free URL shortener instead of Google's own link.
Wikileaks did not publish the original phishing email. If they had the email would have contained headers that may have included the originating IP address, but anyone behind an attack like this will know how to use TOR or a VPN connection to disguise their IP address. The IP address in Ukraine contained in the phishing message is bogus. False information pointing to Ukraine as a possible originating point would be consistent with a Russian attacker, but the attacker could have been from any country in the world.
It is also uncertain whether this was an attack specifically targeted on John Podesta as part of a coordinated attack on the Democratic National Committee, but there is no way of knowing this from the published messages. It is possible it was simply a script kiddie (low level, inexpert hacker) working for a cybercrime group casting a wide net who recognized the name of the phish who had taken the bait and knew the email archive could be worth a greater payoff than the usual email account hack, but there is no evidence either way. The sophisitication level of the attack is within the capability of anyone from a clever high schooler to a state actor. It may have been someone in Russia, but there is no indication it was or wasn't. If the original phishing message was in the archive, a source IP inside Russia would not be sufficient to indicate that the attack actually came from a Russian source - it could simply mean the attacker used a TOR exit node or VPN connection in Russia to hid his actual location.
Who is to blame in the end?
The success of the attack resulted from the confluence of several factors. The young staffers at Hillary For America used sloppy email forwarding discipline which certainly contributed. Charles Delavan should have recognized the fake link, but he told Sara Latham that the Gmail message was real, yet he also included a link to the Genuine Gmail password reset page. Was he really taken in by the fake message, or was he simply telling his end users only as much as they needed? But he should have had some familiarity with the tech capabilities of his end users, and should have communicated accordingly. He didn't communicate clearly and like the other staffers he forwarded a long thread with several messages to Sara Latham, who added her own message to the thread and passed it to Malia Fisher, who forwarded the entire thread to her hapless boss, John Podesta himself.
The Campaign Chair, juggling myriad other tasks and responsibilities, was evidently old-school. Based on the Malia Fisher message that referred to 2-Step Verification, it seems likely that the official hillaryclinton.com Google Apps domain was configured to use the additional security, which requires either a code generated by a mobile phone app or a text message sent to the mobile phone on record whenever someone logs into their email from a new device. This additional security step would have protected Podesta's account from an attack of this type. But Podesta, like his boss Hillary Clinton, wanted to use an off-the-books email address to avoid disclosures of any ethically shady emails like the ones obtained by the attacker. And just as Hillary's off-the-books server, at least initially, was not secured properly, Podesta's personal Gmail account did not use the additional protection of 2-Step Verification. In the end Podesta tried to comply with what the HelpDesk Manager Delavan directed, in the end he was confused by the bewildering chain of emails in the thread, and ended up entering his credentials into the fake website instead of the real Google website in Delavan's email. Podesta thereby handed over his Gmail account to the attacker, giving away everything contained in the very off-the-books mailbox he used for his most private communications. Although the email thread and unclear communications played their parts, it was Podesta's own choice to use an off-the-books mailbox that was unsecured due to his own ignorance that led to the airing of his dirty laundry. The organization he built wasn't capable of protecting him against his own desire to have an off-the-books email account, nor did it have adequate procedures and training for incident response resulting in miscommunication. Finally it was Podesta himself, who gave his password to the attacker.
We will probably never know who was behind the attack. But now at least you know what happened and how it happened - and it's an instructive case for your own email security practices.
- Details
- Hits: 497478

You secure your property with a state-of-the-art alarm system. You chose your neighborhood for good schools, good police and low crime. You may send your kids to private schools to filter what goes into their heads.
Why do you protect your kids on your home network with a basic router anyone can buy at Wal-Mart, or the one the Cable Company put in place?
Consumer grade routers have basic functionality, but they have little or no content filtering capability. When your kids open up a browser on your home network they can be exposed to all kinds of material on the Internet. You should protect what you treasure most - your children - with a Next Generation Firewall that gives you control to filter content like Pornography, violence, gambling, and terrorism, and which gives you peace of mind about everything coming into your home via the Internet.
P3iSys has a great solution to the problem - the Untangle Next Generation Firewall, including Content Filtering by category, Virus Filter, Phishing Filter, and reporting engine. You can also add Firewall Rules to cut off Internet access to any device on your network (for example, you can cut off Junior's access until he cleans his room- a great disciplinary tool) with just a couple of mouse clicks. And you get daily reports which alert you to any violations and the ability to look at everything coming into your home network, all in a reasonably priced firewall appliance with a tiny (less than six inches) footprint that makes no noise. The Untangle Firewall also gives your home network state-of-the-art Data Security protection against hackers.
Want to find out more? Fill out the Service Form at right, or call Rob Mitchell at the office. Installation is quick and easy and included in the price of the Untangle NG Firewall.
- Details
- Hits: 540174
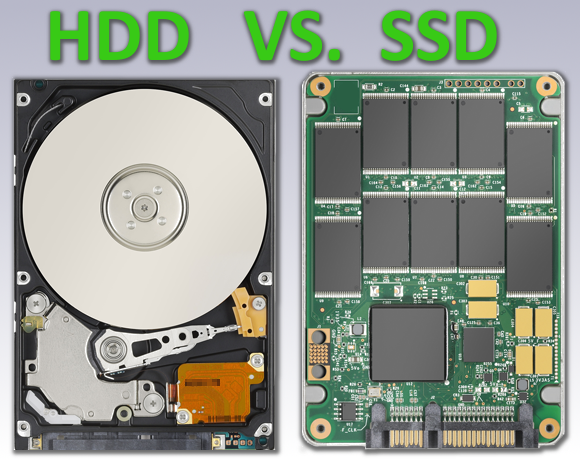
A Solid State Drive can make your PC faster and increase disk space at the same time!
Your PC may be slowing down and running short on disk space. Kill two birds with one stone by switching to an SSD. P3iSys can make it easy. Using cloning software, we can move all of your programs and data onto a new SSD quickly and efficiently, without having to re-install or reconfigure anything.
What's the difference? Your old hard drive is like the one on the left. It has a mechanical platter that spins like an old vinyl LP turntable. The head is like the tone arm on the turntable, and reads the data magnetically encoded on the surface of the disk platter. A new Solid State Drive (on the right) with no moving parts can be up to 10 times faster than your old electro-mechanical hard drive. Usually it takes less than two hours to clone the drive and swap it out. A new SSD will help you get another couple of years out of your notebook or desktop PC.
Want to get the ball rolling right away? Fill out the form at right and a P3iSys Representative will get back in touch with you to arrange an installation appointment!
- Details
- Hits: 722841
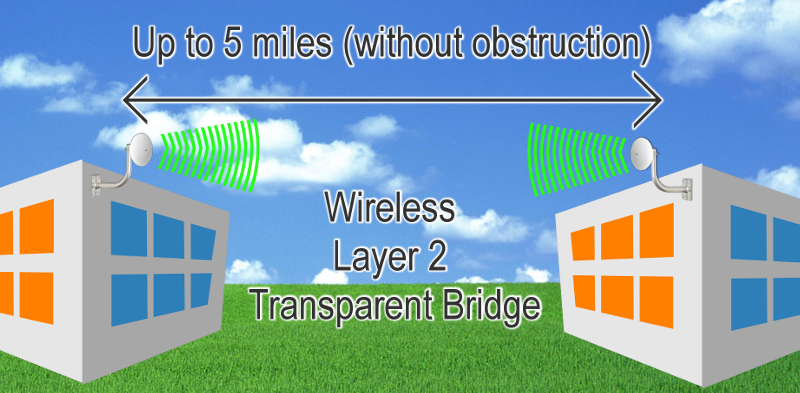
Got a building down on the back lot you need to connect to the office network?
Running fiber between buildings can be expensive! But you can get network and Internet access to that outbuilding without breaking your budget! P3iSys techs have extensive experience with getting network access between sites!
A wireless connection between buildings or sites isn't complicated - it consists of two wireless units configured in what is called a Layer 2 Transparent Bridge, and apart from the wireless units themselves, requires no special or sophisticated network equipment. To the computers and devices on each end, the link looks like a network switch. It's a little slower than fiber, but MUCH less expensive, and can provide reliable connectivity to outbuildings, garages, and construction sheds.
For just a few hundred dollars, including installation, you can have a high-bandwidth connection to that site or building where fiber was too expensive or not possible due to property issues.
Getting connected begins with a site survey - we can do a preliminary survey very quickly at no cost to you - more complex implementations may require an extended site survey where there are terrain or other issues. Call P3iSys today to get started and find out if a wireless link is appropriate for your needs and environment.
- Details
- Hits: 696287
View all Email attachments as suspicious!
Ransomware has gone from obscurity to being headline news, and has become the Number One Cyber Threat facing businesses and organizations today. The threat has emerged for a very simple reason: Ransomware is fantastically profitable for cybercriminal gangs. Russian gangs alone made over $135 million net profit from ransomware in 2015, which started out with only a few variants, and has since exploded onto the Internet with dozens of new variants and delivery modes, all aimed at extorting money from businesses and organizations by encrypting all files on a PC and on a network the PC is connected to.
Click Here to Read More>> Ransomware! The New #1 Cyberthreat to Small Business


